Newsletter Subscribe
Enter your email address below and subscribe to our lovely newsletter.
*We do not spam & you can unsubscribe at any time.
Enter your email address below and subscribe to our lovely newsletter.
*We do not spam & you can unsubscribe at any time.

*This post may contain affiliate links. If so, we may earn a small commission when you make a purchase through links on the site. This is at no additional cost to you. Read full disclosures here
There are tons of different snoopers online who could discover your identity in different ways. And then there are services that require you to reveal your online identity in order to use them. Let’s find out who might be snooping on your online activity behind your back.
Whoever owns the Wi-Fi network you connect to has a great deal of power over your internet connection, including the ability to monitor what you do. Plus, on unsecured public networks, there are ways for other participants to see what other people are doing as well.
Most websites use trackers and cookies too. Cookies can be useful because they can save login sessions or shopping baskets. However, they also play a huge role in creating your ‘user profile.’ This personal information of who you are and what products or ads you’ve engaged with can then be sold to third parties. You can avoid this by deleting cookies manually after each browsing session or installing various browser plugins.
Because your ISP processes all of your traffic, they have extraordinary access to everything you do online. In most countries, they are given broad rights to profit from their internet data or to share it with government surveillance agencies.
If you aren’t using a VPN, your ISP can see what websites you visit (via their IP addresses) and how much time you spend there. They know who you are and your original IP, so without a VPN, they can trace any information back to you. In the US, they don’t even need your permission to record, share or even sell your browsing history.
With VPN software enabled, your ISP can no longer see what you do online. However, your ISP will always know your real IP address because they’ve assigned it to you. You pay for the service so they need to keep a record of your personal and payment details. The only way to cut them out of the loop is to use someone else’s internet (like public Wi-Fi), but you’ll still need a VPN so they can’t see what you’re doing.
The anonymity a VPN provides against government surveillance will depend largely on the surveillance methods your government uses. The tools a government would have at its disposal far exceed the scope of protection a VPN provides. As far as just your internet connection is concerned, however, a VPN can go a long way to keep you private.
However, keep in mind that there are countries where VPNs are blocked or considered to be illegal. In oppressive regimes with strict online censorship laws, governments want to have full control of cyberspace. As a result, they find ways to track you and invade your privacy. In some countries, only government-approved VPN are allowed, and approval usually means letting the government monitor those VPNs’ users.
Websites need your IP so they can send you their content. Unless you’re using a VPN, that IP will be your real IP address, revealing your location and potentially other information about you. Even with a VPN, the websites can see the operating system and the browser you use, the plugins you have installed, your CPU and even whether you are currently logged into any social media platforms. Do you trust every website you visit with that information?
A VPN won’t stop you from collecting cookies – only your browser can do that. However, with a VPN, you can prevent websites and their cookies from discovering your real IP address.
Any website you upload anything, including but not limited to social media, will be able to see your metadata as well – if you have it. Metadata is data attached to your digital documents and photos that can reveal who created the document, what organization they’re a part of, when it was edited, and the device and even the software used to create it. Metadata is generated automatically for most types of documents, but it can be manually stripped off.
Social media platforms make money from ads, so it’s in their best interest to get as much information about you as possible. From your email address and the pages you liked to the friends you interacted the most and what your face looks like – they know it all.
Your anonymity on social media depends on how much data you give up, but they generally require quite a bit just to sign up. If you willingly share this information with social media networks and the people on them, an anonymous VPN won’t protect you. You’re not protecting your privacy if you keep your social media profiles public or openly share sensitive information. If you forget to disable your location settings, social media giants and everyone else can see where in the world you are every time you post anything online. Make sure your social media profiles are as private as possible.
Similarly to other social media platforms, this tech giant built their business on trackers and advertising. However, the worst part about Google is that it owns a huge number of different platforms and the more apps you use, the more information they gather about you. The “user profile” they create is pretty accurate and includes a lot of personally identifiable information like your location, age, gender, things you’ve searched for, videos you watched on Youtube. Let’s not forget that Google tracks your location even if you disable your settings.
It uses face recognition technology to scan your photos, its robots crawl through your Gmail and Google Drive documents, and Chrome tracks all the websites you visit and ads you’ve engaged with. This information is used to feed you ads. You should learn how Google tracks you and look for privacy-oriented alternatives.

Recommended reading:
The best private browsers to use
Your credit card and digital payment platforms also leave a trail and can be personally identifiable. They can reveal where and when you shopped, where you boarded the train and where you got off, and which cities or countries you traveled to. Most financial systems require this level of identification, so maintaining anonymity without using cryptocurrency or cash is difficult. This is why privacy-focused companies like NordVPN now accept payments in cryptocurrency.
We place a great deal of trust in apps from the moment we download them onto our devices. Almost every app will ask for permission to access certain parts of your device and you’ll need to grant that access to use them. What they do with that access is up to the app’s creators.
And then there are the apps we share our private data with – messaging apps, image editing apps, and others. If you want to stay anonymous to others while browsing the web, this might not change much, but the app’s creators or service providers could still potentially access all of that identifying and private data.
When you download an app, make sure you trust the developers. Also, look for any that have good security and privacy features. For example, you can choose a private and encrypted messaging app over some of the more popular options.
Don’t let your credit/debit cards out of your sight – ever!
Many are guilty of handing over their credit card to waiting staff in a fancy restaurant, and it is these very same high-end establishments that dishonest staff target – because they know you have money to spend!
A simple ‘skimming device’ to copy your card details is all that’s required to duplicate your card, and there are still plenty of places a scammer can use your card without knowing your PIN. If you have been particularly unguarded and they have managed to take note of your PIN as well, then you are guaranteed misery.
It is also very common for skimming devices to be installed on ATMs abroad, so be extra vigilant when using them.
How many times have you got the check for dinner and just handed your credit card to the server? This practice is not safe and travellers are more vulnerable than locals because it’s assumed it’ll take longer for them to notice and they won’t be back. Rather than handing over your credit card (i) get off your butt and pay at the host stand, (ii) use a mobile wallet or (iii) pay in cash.
If you are unfamiliar with how secure you computer, tablet and smartphone(s) are, then they probably aren’t very secure at all. Your attitude towards online security needs to change immediately!
Thousands of expats fall victim to electronic fraud and the problems are epidemic. Things have progressed away from Nigerian billionaires needing your help to move money into your account and modern scams are very clever and often sophisticated.
It is important that you understand many of the tricks and techniques behind the most popular online scams. Understanding and being able to recognise such cons is the best way to avoid falling victim to them.
Beware if:
Remember – your bank and other reputable financial institutions will never:
Here are a few of the most typical online scams:
Email scams are among the most common. You might receive an email offering a sum of money in return for helping someone to move their money to another account, or overseas (this is known as a “419 email”).
Phishing emails are designed to trick you into revealing personal information or passwords, and pharming emails lead you to a convincing website in order to access your information.
There are also investment and pension scams, which might offer shares, or the chance to convert your pension pot into cash.
These usually happen through online dating websites, but scammers may also use social media or email to make contact.
They might express strong emotions for you in a relatively short period of time and suggest you move the relationship away from the website to a more private channel, such as phone, email or instant messaging.
Once they’ve gained your trust, they’ll ask for money and gifts, even your banking/credit card details. They may pretend to need the money for some sort of personal emergency.
Never send money to someone you haven’t met in person. Consider the possibility that the approach may be a scam, particularly if:
More and more of us are shopping online now, but if you spot a great online offer which is “too good to be true”, it probably is.
Since it’s so important for your privacy and online security, you should be as careful protecting your social media accounts as you are protecting your banking and email accounts.
“Money flipping” scams are increasing on social media, where profiles show luxury goods and promise to deposit money into an account. The scammer may pose as a bank or luxury retailer, and may talk about investment opportunities. Social media is popular for these type of scams, especially on platforms with the ability to DM people who aren’t mutual follows. As a general rule, if it sounds too good to be true, chances are that it probably is.
i. Only use certified apps provided by the institution you are dealing with. If in doubt visit their website and use their links to download an app or be redirected to the legitimate Apple or Google Play Store.
ii. Avoid using third party intermediaries, or agents who offer to make transactions on your behalf.
Don’t let them get away with it!
One of the very best ways you can secure yourself whilst online is by using a Virtual Private Network (VPN). They act as a middleman between your device and the internet. All communication between your device (computers, tablets, smartphones) and the internet is encrypted ‘end-to-end’ making your data illegible to hackers. (Public WiFi hotspots are a favourite haunt of hackers)
If you use online banking in the U.K. (or anywhere else for that matter) your bank is likely to have security measures in place that make it very difficult to access their online banking systems from abroad. Many expats (and tourists) don’t realise this and get caught out. To avoid issues logging-in a VPN can make it look like you are still in the U.K. (or any other location you choose) enabling you to access your bank’s online platform.
Without a secure VPN many expats & tourists suffer great inconveniences. Don’t be left high & dry. A good VPN is invaluable for expats and a definite must have essential!
By definition, a VPN is your best friend when using public Wi-Fi. Hackers have many methods to steal your data on public hotspots, but using a VPN means that you can stop worrying about that. Therefore, people who want to browse in full privacy should use a VPN to secure their connection.
If a public Wi-Fi outlet alerts you that your data may not be secure, don’t ignore the warning! Avoid using public Wi-Fi to log into sensitive websites, like your bank account. And look for websites that have an “S” in the url, like: https://www rather than http://www. The “S” stands for secure, meaning the website has some encryption for added security.
If you use your laptop in public often, at the very least get a security plug-in like “HTTPS Everywhere” to give you some extra security automatically. Best practice is to only store, sync and access your sensitive data via a securely encrypted online ‘Vault’. I use the free NordLocker and recommend you do too. It is explained further in this guide, or you can hop-over and read all about it on their website.
Get it here for FREE.
Contrary to what you might read elsewhere – Never use a public computer to access anything sensitive.
Just remembering to logout of a public computer is simply not good enough!
Naked Expat
Key-logging (spy) software might be installed on the public computer to remember what you have typed – effectively giving scammers a ‘playback’ of what you accessed and the passwords you typed!
One of the most popular things a VPN is used for is content access. If using streaming services and social networks while abroad is important to you, a VPN can help. It changes your IP address and redirects your connection to the internet through a remote server.
Using a VPN is a good idea even when browsing from your home. VPN encryption is important when you want to protect your internet traffic and minimize your online footprint. This way, your internet service provider won’t be able to sell your entire browsing history to the highest bidder.
People working in countries with limited freedom of speech rely on private internet connection for their work. Sometimes, their lives might depend on it. Someone who lives under an authoritarian regime should use a VPN to hide their IP address and ensure extra security for their sensitive messages.
Government agencies track and collect your browsing activity, messages, social posts, and other private data. A VPN protects you from that by encrypting your traffic and hiding your IP address. Use it at home, at work, and on the go to enjoy non-stop protection.
People who like gaming online have to deal with DDoS attacks, bandwidth throttling, and content restrictions. Luckily, you can forget about all of these problems with NordVPN. If you’re serious about gaming and want to enjoy a stable and safe connection, you should use a VPN.
When you download VPN software to your device, it does most of the work for you — you only need to log in and connect.
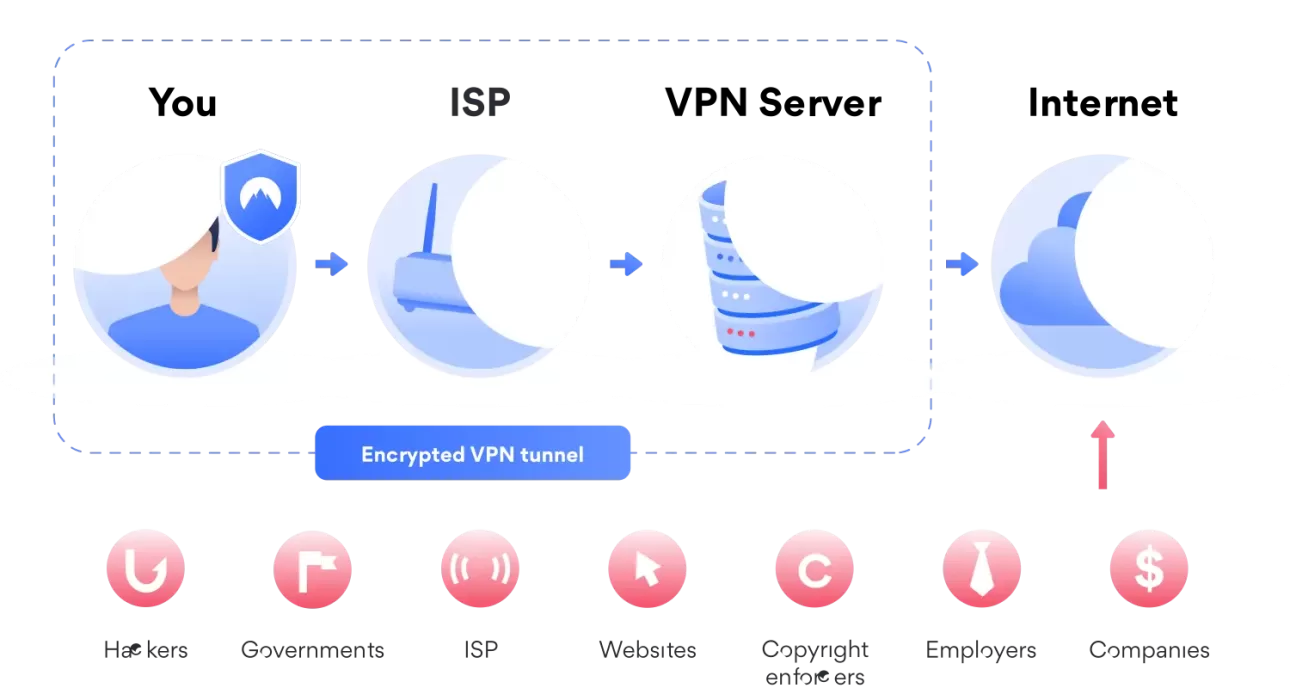
However, it’s helpful to know how a VPN works to understand the service better. Here’s what’s going on behind the scenes:

People turn to VPNs for different reasons, and whatever yours is, you need to ask three questions before choosing a provider. How fast is it? Will it keep my data safe? And will it respect my privacy? Of course, you want your connections to be safe and your data to stay private. But to have all that without losing any speed? That’s the trick. So when you choose a VPN service, make sure they don’t make any compromises – there’s no point in having unbreakable encryption if every website takes ages to load.

Price is one of the most important factors, no matter what product you’re buying. And if a free option comes up, people are naturally interested. But when it comes to free VPNs, it’s better to steer clear of them. Remember – you’re looking for speed, security, and privacy, and with free VPNs, you’re unlikely to get any of these features. These providers usually don’t invest in their server network or maintenance, so their VPN connections might be unstable and leaking users’ IP addresses. They also must make money somehow – usually by selling their users’ data. So instead of looking for the cheapest option, try to find a VPN provider you can trust. I have used NordVPN for over 10 years now and I am very confident in recommending them here.
NordVPN offers dedicated apps for all major platforms. And you can protect up to six devices with a single account. Install it on your phone, laptop, your kid’s iPad, Smart T.V. or your Wi-Fi router!
Don’t want to encrypt your entire device? Use the split-tunnelling NordVPN feature and select which apps connect to NordVPN and which stay on the local network.
A private VPN will make it very difficult to track your online activity. It all depends on what sort of tracking you might be subject to and what you’re doing. If you’re using Chrome connected to your Google account, it doesn’t matter that your traffic is encrypted. Google will know what sites you visited and the content you interacted with. Your ISP or the government won’t be able to tell what you do online after you connect to the VPN server – but they may be able to ask Google.
If you live in a totalitarian regime that has highly restrictive internet rules, the authorities will be able to tell that you connected to a VPN, but not what you did afterward. However, NordVPN has a feature called Obfuscated servers that will help make your VPN-secured connection harder to detect.
Yes. While it’s practically impossible to grant absolute anonymity online, NordVPN does everything it can to provide fast and reliable security and privacy. We have an industry-leading list of powerful features to help you stay anonymous, but even so, you’ll need to take other precautions to stay anonymous. With that being said…
Here are just a few of the features that help NordVPN keep your information as private as possible:
Introduction
There is a lot of valuable information in this guide about protecting all your personal data, be it financial details, photos/videos or anything else you don’t want a hacker to access.
The most common crimes expats fall victim to are identity theft and credit card fraud. The vast majority did little to protect themselves – especially now most of us have smartphones which can contain a vast amount to useful data to any would-be hacker or scammer.
If you really can’t be bothered to take all the steps necessary to protect your personal data outlined in this guide, at least do yourself a huge favour and strip-out all unnecessary Apps and stored files from your Smartphone.

You should never have apps on your smartphone that access sensitive data. You are more likely to loose your smartphone than you are your computer, so store all your valuable data on your computer – encrypted – and “in the cloud”. This way no one but you (or whom you permit) can access your encrypted data and it’s useless to a hacker when encrypted.
Only use Apps that are absolutely necessary. Any “payment apps” should be kept to the absolute minimum and definitely do not instal Apps to access investment portfolios or trading. All sensitive activity should be done in a secure, encrypted manner using a dedicated online ‘Vault’.
Similarly, if your computer gets stolen or blows up, it doesn’t matter – because you can easily login from another computer and access your files – everything is encrypted “in the cloud” not on the local computer!
(Make James Bonds’ “Q” proud!)
Radio frequency identification technology (RFID) lets you wave your credit card in front of a reader to transfer your credit information, effectively avoiding traditional skimmers and giving your card to a stranger. But what if a hacker has an RFID reader?
A simple RFID blocking wallet, or even a few layers of heavy aluminium foil can block their efforts.
When using the Internet, most people know to use encryption of data in transit. This is the big difference between HTTP and HTTPS traffic (i.e. whether or not the lock icon shows up in the address bar).

Using HTTPS helps to ensure that you’re connected to the right website and that no one can eavesdrop on your connection, which may include personal data like credit card information, your location, your Netflix account etc.
However, your personal data isn’t only at risk when it’s traveling over the Internet. Despite your best efforts, there is a chance that your computer will be infected with malware that your antivirus doesn’t catch. If this is the case, the malware may start looking for sensitive data on your computer and send it to the cybercriminal running the malware.
This is where file encryption comes in. Instead of just encrypting data in transit, file encryption ensures that data is stored encrypted on your computer. This means that an attacker or malware with access to your computer can’t read your sensitive data unless they also know your password. I use NordLocker and recommend you do too. Get it here for FREE.
The most common argument against implementing good cybersecurity practices is “I don’t have any data worth stealing”. However, this statement is incorrect, and cybercriminals commonly target individuals to steal personal data.
When thinking about your personal data, you might focus on credit card and banking information, which is primarily entered into the browser and not stored on the machine. A great deal of personal data can be extracted from files that you may store on your computer without thinking twice about them. Some examples of these files include:
Most financial software and online portals provide an option to store a copy of the file on your computer. A tax return or similar financial files provides an attacker with all of the information that they require to perform identity theft. Similarly, Pension Forecasts, DVLA, and other common forms can contain sensitive data.
By default, many cameras and smartphones will embed location information in photos, which is why your computer can tell where and when the photo is taken. A picture of a backyard barbecue can reveal a home address, or a birthday photo reveals someone’s name and date of birth.
Applications for a loan, rental, etc. often contain sensitive information like a social security number. This information can be used in identity theft scams.
When booking a vacation, you may store a copy of the booking information on a computer. These confirmations can include financial information, information about your travel plans, and provide a would-be burglar with a list of dates when a house will be empty.
The latest trend in ransomware is to steal all your data which is then used to blackmail you into paying a ransom. If you don’t pay, your data is leaked to the internet, used for Identity Theft or sold to the highest bidder. Scary stuff!
The good news is, if your files are encrypted, the cybercriminals do not have access to your data, instead, they can only see scrambled data which is useless and cannot be held to ransom. File encryption can help defend against Ransomware.
Sharing files online is more popular than ever. You do it on social media like Facebook, on messenger apps, forums, and cloud services. But what’s the risk? Only the people I’ve sent the file can see it, right? Wrong!
If your shared files are not encrypted, they’re accessible to everyone. Imagine the devastation of finding your private pictures or bank number scattered across the web…
The reason why it is important to encrypt files before sharing is simple – encrypting your files ensures your privacy. Someone unauthorised can’t open the files, meaning only you and your intended recipient gets access.
Employees are increasingly using mobile devices for work. This trend has become more common in recent years, and the COVID-19 pandemic created an explosion in telework and the use of personal and mobile devices.
With the increased convenience of these mobile devices comes higher cybersecurity risk. A smartphone, tablet, or laptop is relatively easy to lose or have stolen in a public place. If this occurs, the thief may be able to read sensitive personal and company data off of the device by scanning its hard drive.
File encryption protects against the threat of lost or stolen mobile devices. Each file on the machine is encrypted, and the encryption keys are stored protected by the user’s password. If an attacker doesn’t have access to this password, then they can’t read any useful data off of the stolen device. Get NordLocker here for FREE.
File encryption is a valuable tool for data security. However, implemented improperly, it can lull you into a false sense of security. Some vital features to look for in a file encryption solution include:
A lot of encryption products use such terms as ‘Military-graded’, ‘Bank-level’ or other marketing phrases which on paper sound really impressive, but let’s get real here, who actually knows what encryption algorithms the military use? Looking beyond those marketing phrases and claims, you’ll want industry standard, unmodified AES encryption, preferably, independently audited.
Some encryption solutions use a single key to encrypt all your files and data, but this forces an ‘all or nothing’ approach and puts all your data at risk should your key fall into the wrong hands. A good file encryption solution should encrypt each folder or file with a unique key which minimises the risk of all your data being breached should a key be hacked or stolen. Additionally, if you suspect a key has been compromised, your encryption solution should allow you to change all your file keys with ease.
Your files should be encrypted at all times and when editing, any changes should automatically be saved and encrypted.
NordLocker encryption protects your data. It gives you a choice over what you share and what always stays private. No data-harvesting corporations or hackers can access your encrypted files.
Encryption is compatible with files of all types and sizes. Whether it’s a tiny PDF from work or your holiday in HD video, you can use encrypted file storage to secure it all.
NordLocker’s file encryption has no limits. If you wanted to encrypt every file on your computer, you could.
Sync your data privately. NordLocker’s end-to-end encrypted cloud ensures that you alone can see your files — on any computer. No matter where you are, your encrypted file storage is always just a few clicks away.
Need an important file? Log into your account on any computer, and NordLocker will fetch it for you.

In over 15 years as an expat myself, I have lost count of the amount of other expats and holidaymakers who have fell victim to scammers and data theft. Let’s face it, technology makes our life as expats and living abroad in another country much more convenient and straightforward than it ever used to be. But! (there’s always a but)
Unfortunately the increased reliance on technology hasn’t gone hand-in-hand with an increase in data security awareness.
Ignorance is bliss – unless you become a victim of data/identity theft or credit card fraud. Then it’s a nightmare!


Remove all Apps from your Smartphone that are not absolutely necessary.
Get a VPN: (i) Encrypt your date whilst online. (ii) Save up to 72% on NordVPN vis this Special Offer. (ii) Enjoy watching UK TV like BBC iPlayer, Netflix UK etc abroad: Read more
Online Vault: Secure your files/data with an online encrypted “Vault” – You did read this article (above), right? If not, go back and read it again!
Simplify: Remove all Apps from your Smartphone that are not absolutely necessary. Reminder of why you should this.
Save up to 60% using this link

Encrypt your data when online +
Start enjoying UK T.V. from abroad, including:
BBC iPlayer, ITV Hub, Netflix (UK) (USA) and more.